Blog
Sophisticated Ransomware: Mitigating the Risk of Infection
Worms, Viruses and Malware are only some of the threats that the Internet can...
Giving Back to the Community Builds Company Morale
People who work for computer consulting companies and other small businesses...
Training Increases Employee Retention
Employees make the company. Without them there is no way to get work done, yet...
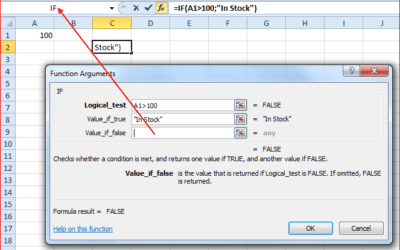
Excel Logical Functions Webinar
Some of the most common and powerful functions for Excel users are “logical...
A Look at the Lenovo MIIX 700 Series – The New Leader in Tablets for Your Mobile Workforce
Are you looking for a way to mobilize your workforce with hardware that...
Common Myths about Network Security
Do you think your computer network is safe from being hacked? With all of the...
Network Security Webinar Series – Social Engineering Fraud
Learn how to identify: CEO/Email Fraud Phishing & Spamming Baiting Caller...
How Will You Deal with the Internet of Things?
Experts estimate that by the year 2020 a whopping 50 billion devices will be...
Are You Ready to Recover from a Disaster?
Spring is here, and it can bring either great weather or crazy storms. When...
USCC in the News – Thomson Reuters Article
IMPACT ANALYSIS: Should Firms Pay 'Ransomware' Demands? Responding to New...
Employees Are the First Line of Defense against Cyber Attacks
IT departments like to think of themselves as modern knights of old. They are...
Features you didn’t know existed in PowerPoint Webinar
Microsoft is always adding new features and improving on existing ones to make...