On May 26th, Microsoft alerted users warning of a new strain of Ransomware called ZCryptor, which works like a worm and spreads via network and removable drives affecting more users. This ransomware is malicious software that encrypts computers typically via fake installers like Adobe Flash, malicious spam, or bogus macros in MS Office documents.
Pull the Plug
Upon entry into the unsuspecting user’s computer, ZCryptor encrypts the user files. The ransomware actually distracts the user by displaying a popup, which confuses the user and creates time for the malware to run. The popup continues to appear while the malware is encrypting the computer. If you see the popup below, pull the plug on your computer.
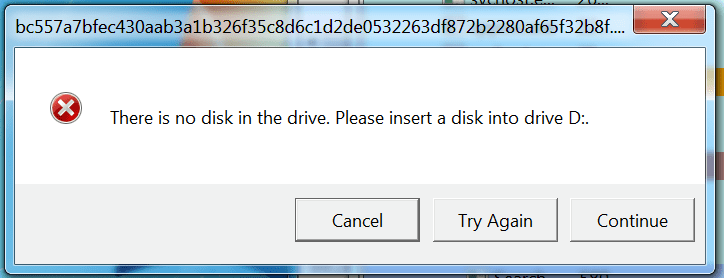
A fake Windows Error popup for the ZCryptor Worm
Worrisome Worms
ZCryptor’s ability to spread itself to nearby targets marks it as a first of its kind. This is particularly worrisome because so many devices on a network can be infected in one go. Microsoft reported that the ransomware targets 88 types of files and that number is growing as ZCryptor continues to mature.
Once the encryption is complete, ZCryptor’s ransom message is revealed which asks for $500.

ZCryptro Ransomware Worm Error Message
Don’t Spend a Penny & Minimize Downtime
There is no identified way for ZCryptor affected users to recover their files for free, unless they have a secure backup. Users with secure backup and disaster recovery solutions such as Datto, can be restored in minutes without paying a penny. U.S. Computer Connection helps business and healthcare in Connecticut and New York with IT consulting which includes secure backup and disaster recovery. For user education and to learn more about ransomware register at uscomputer.com/events for Ransomware, June 7th.

